In an era where data breaches are common, and cyber threats are on the rise, it’s important to ensure that your data isn’t at risk of being stolen by hackers. If you run a business, protecting yourself from a ransomware attack is not only vital to the health of your company but also to its employees. This guide will walk you through practical steps you can take today to prevent a future attack.

Common ransomware infection
• RDP Servers: It is hard to imagine that in today’s IT world there are still many RDP servers that are directly connected on the internet . The reality is internet-connected RDP needs to stop. The fact that over half of ransomware comes in through RDP tells us that exposing RDP to the internet does not align with a forward-thinking ransomware resiliency strategy .
• Phish Email: The other most frequent mode of entry is through phish email . We’ve all seen emails that just don’t make sense or look right . The right thing to do is delete that item, but not every user handles these situations the same way . There are popular tools that can assess the threat risk of phish success for an organisation . These tools can be effective in measuring an organisation’s competency in being able to self-assess the risk of phishing emails, attachments and more.

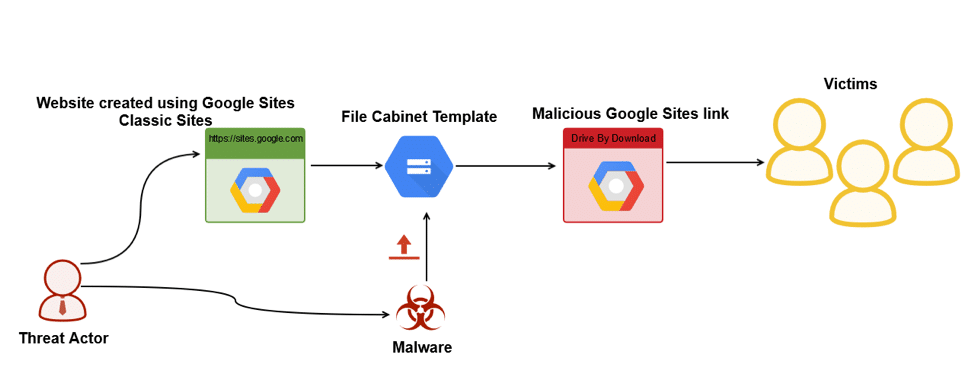
• Visiting Infected website: A drive-by download is any download that occurs without your knowledge. Ransomware distributors make use of drive-by downloads by either hosting the malicious content on their own site or, more commonly, injecting it into legitimate websites by exploiting known vulnerabilities. When you visit the infected website, the malicious content analyses your device for specific vulnerabilities and automatically executes the ransomware in the background. Unlike many other attack vectors, drive-by downloads don’t require any input from the user. You don’t have to click on anything, you don’t have to install anything and you don’t have to open a malicious attachment – visiting an infected website is all it takes to become infected.
3 Ways to prevent ransomware
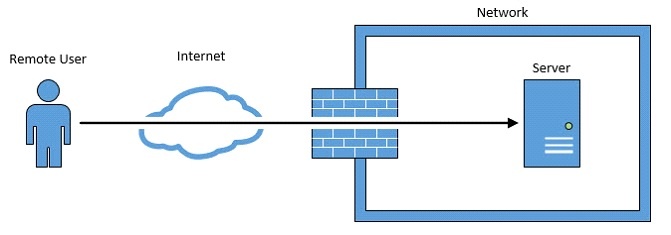
• Reduce the attack surface: A VPN will ensure that a computer using an RDP will not be directly accessible to other users. This ensures that no hacker got get access to the computer. Limit access to certain applications for certain groups of users and for certain portions of the network. With high visibility and the right policies, a large majority of the methods attackers use to deliver malware attacks on your network can be cut off.
• Prevent known threats: Using reputable ransomware protection tools will prevent users from inadvertently downloading a malicious payload or having their credentials stolen by preventing access to known malicious and phishing URLs. Blocking these threats removes them from the equation entirely. Use

• Backup: The key to not having to pay ransom is having the backups to restore systems that ransomware has encrypted. And the key to protecting those backups from ransomware is to put as many barriers as you can between production systems and backup systems. Veeam backup products are known for being simple, flexible, and reliable. Practice 3-2-1 Rule as a general data management strategy. The 3-2-1 Rule recommends that there be at least three copies of important data, on at least two different types of media, with at least one of these copies being off site . The great part about the 3-2-1 Rule is that it does not require any particular type of hardware and is versatile enough to address nearly any failure scenario.

Remediation
Despite all of the education and implementation techniques employed to be resilient against ransomware, organisations should still be prepared for the worst-case scenario . The approach to remediating ransomware as:
• Do not pay the ransom
• The only option is to restore data
With the recommendations previously outlined in this article, organisations should be prepared to have layers of resiliency to defend against a ransomware incident.
Conclusion: For businesses, the threat of ransomware attacks is real. However, with the proper education, technology, and support, organisations can keep their internal and customer data safe and secure. With the right preparation, the steps outlined in this article can help increase your resiliency against a ransomware incident to avoid data loss, financial loss, incur damage to the business’s reputation and more business reputation damage and more.
You can find more information about Veeam ransomware resiliency resources at: http://vee.am/ransomwareseriespapers . At Infosyte we offer Veeam Certified Engineers (VMCE) and for those interested in finding out more, please visit us here.



